Creating a secure IT environment is essential for businesses and organizations, but can often be complex. To ensure a strong security landscape, an array of technologies should be employed including authentication methods, encryption techniques, firewalls, intrusion detection systems (IDS), and Virtual Private Networks (VPNs).
Each of these has its function in providing maximum safety, ranging from preventing unauthorized access to data transmission protection. By carefully implementing the best approaches available, businesses can create a secure IT environment that allows them to operate with confidence and peace of mind.
Authentication Methods
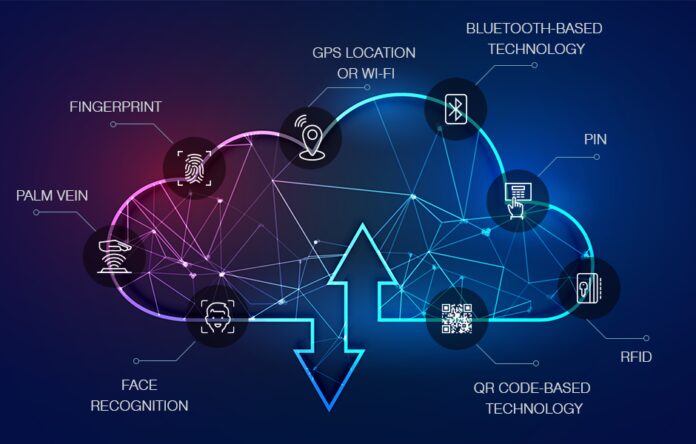
Authentication is an essential step in keeping data or systems secure, as it verifies that the person trying to access the information is an authorized user. Authentication involves the use of passwords and usernames, or biometrics such as fingerprints, voice scans, facial recognition, and iris scans. This verification process limits access to those who have proper identification and keeps any unauthorized users out.
To ensure an even higher level of security, Multi-Factor Authentication should be employed as an added layer of protection. It requires multiple pieces of evidence before allowing access to protected resources – for example, two forms of identification such as a password plus a fingerprint scan – making it more difficult for unauthorized access. Employing Multi-Factor Authentication safeguards sensitive resources against potential security breaches by verifying user identity more stringently.
Encryption Techniques
Data encryption is an incredibly useful tool for protecting confidential information from unauthorized access. By scrambling data results into a seemingly random string of numbers and letters, it can only be decrypted by a set key given to the intended recipient. In most cases, symmetric encryption is used which works with just one key for both encrypting and decrypting data.
The use of this single-key system makes encryption relatively simple and effective, though it’s important to keep the key secure and hidden. Asymmetric encryption provides an additional layer of security through the use of two separate keys; a public key meant for encrypting data and a private key meant for decrypting that same data. For large organizations dealing with sensitive data, this additional level of complexity greatly boosts security without having to share or even store the single-key system integral to symmetric encryption – making it the preferred option in many circumstances.
Antivirus Solution

An antivirus program is a necessity for any computer system, as it can help protect against malicious code that can otherwise cause a lot of damage. These programs are designed to scan a computer and detect anything suspicious or malicious, allowing users to safely remove it from their systems.
They also allow users to isolate the offending code, so their systems can stay secure whilst taking other measures. Installing and frequently updating antivirus software is essential for anyone who is connected online – not just to protect the device itself but all devices in the network too.
Proper protection will go a long way towards preventing viruses and malware from infiltrating your device, ensuring optimal performance and security at all times.
Cloud-Based Security Solutions
Cloud-based solutions for businesses have been gaining traction as they provide an additional layer of security to supplement traditional data security measures. The remote storage capabilities of cloud-based systems keep sensitive company data and applications away from on-site networks, so they are better guarded against potential security threats. Furthermore, the advanced features such as monitoring, reporting, and analytics in cloud security packages help organizations quickly identify any suspicious activity within their networks.
Firewalls

Firewalls are an essential part of any organization’s cyber security plan, providing a barrier between external threats that can compromise an organization’s data. Firewalls are designed to block malicious threats, detect any suspicious activity such as malware or viruses, and provide insight into network activity by examining incoming and outgoing traffic.
Additionally, firewalls can also be used to implement security protocols that limit access to certain web services or URLs. Not only do they provide vital protection against cyber threats, but they can also help organizations enforce key security policies to ensure data remains safe and secure.
Intrusion Detection Systems
An Intrusion Detection System is an essential security feature of any modern computer network. It works by constantly scanning the traffic flowing through a network and looking for patterns that might indicate malicious activity.
Intrusion Detection Systems have become increasingly sophisticated, allowing them to identify known attack patterns, malware signatures, and other signs that represent potential threats to data security. In the event of an intrusion being detected, the Intrusion Detection Systems can promptly notify system administrators so that they can take necessary steps to protect their networks from further harm.
Intrusion Prevention System
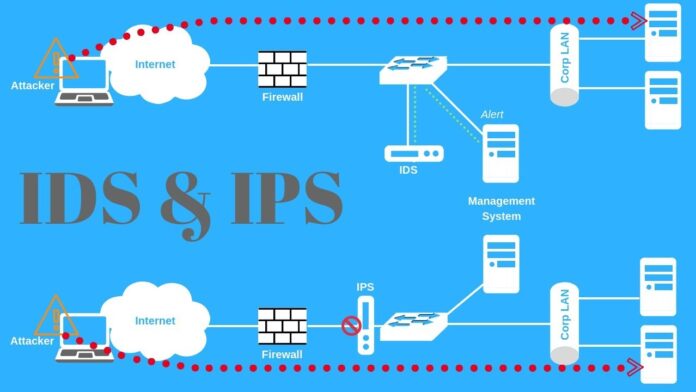
An Intrusion Prevention System is a powerful cyber security system with the aim of detecting, analyzing, and blocking any malicious activities on a network. It offers enhanced security features compared to other detection solutions because it utilizes more sophisticated technology to uncover potential threats earlier and take action before serious damage can be done.
A well-configured Intrusion Prevention System allows companies to better respond to cyber threats by providing them with increased visibility into their systems and allowing them to block specific types of traffic or networks that seem suspicious. This type of advanced software provides organizations with an additional layer of defense against those trying to compromise confidential information and disrupt normal business functions.
Virtual Private Networks
Virtual Private Networks are incredibly beneficial to businesses and other organizations that require secure connections between two networks. The data that is shared over a Virtual Private Networks connection is encrypted, preventing any unauthorized access. This ensures that the information being exchanged is kept away from prying eyes and can’t be altered in any way.
An additional benefit of a Virtual Private Networks connection is that it allows people at different locations to access one unified network securely. This simplifies communication across multiple offices by allowing everyone to access the same resources, even if they’re located in different states or countries.
Security Incident and Event Management
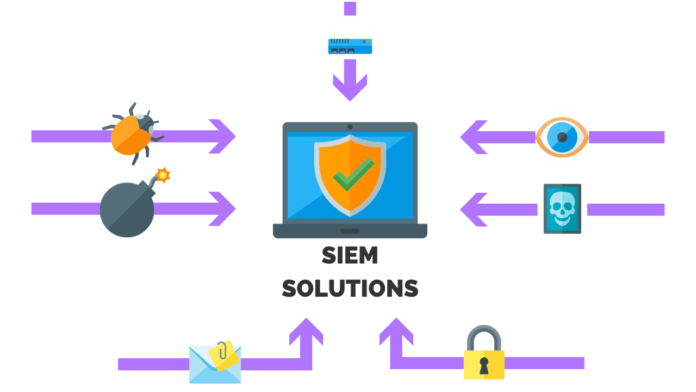
Security Incident and Event Management is a powerful technology used by organizations to identify, investigate, analyze and respond to potential cyber threats. This critical security solution provides a unified view of an organization’s IT environment by collecting data from multiple sources such as user access logs, system events, application logs, and network flows. By storing this information in one location, Security Incident and Event Management systems can more efficiently detect unusual activity and determine if there is any threat present. Additionally, once a threat has been identified, the data collected with Security Incident and Event
Management systems make it easier for an organization to investigate the issue further and take necessary action that will mitigate damage before it becomes more serious.
Conclusion
Businesses of any size or scope need to make sure they have a secure IT environment. Without proper protection and security measures, confidential data could be exposed to malicious actors or cyber criminals, which can lead to financial losses, reputational damage, and possibly legal action.
Fortunately, there are several proactive technologies companies can employ to keep their IT infrastructure safe such as authentication methods, encryption techniques, antivirus solution, cloud-based security solutions, firewalls, Intrusion Detection Systems, Intrusion Prevention System, Virtual Private Networks, and Security Incident and Event Management. A secure IT environment is essential for any business, so be sure you take the appropriate steps with the right tools and technology to protect your data today.




